Under Attack: Trucking industry increasingly at risk of cyberattacks
After being a strong proponent and early adopter of electronic logs, it was back to paper logbooks and old-fashioned dispatch by phone for a portion of Bison Transport’s fleet in early September. About 100 trucks lost access to Orbcomm electronic logging devices (ELDs) and fleet management software Sept. 6, after the vendor suffered a ransomware attack.
“As soon as we aware of the outage, we immediately notified our drivers to let them know there was a disruption in communications and then gave them the green light to communicate using emails, texts, and phone calls,” Brad Gerrard, chief information officer with Bison Transport, told Today’s Trucking. “We jumped to paper logs in short order.”

The U.S. Federal Motor Carrier Safety Administration issued an exemption, allowing those affected by the outage to use paper logs until the problem was resolved, or to Sept. 29, beyond the normal eight-day allowance. For Bison, the outage affected only a small portion of its fleet, but it was still a major disruption that put its disaster readiness to the test.
“We were able to adapt and react pretty quickly,” Gerrard says. “But there were clear takeaways, like the need to make sure we have alternative means of communications, up-to-date contact information, and other ways to update drivers on what they should be doing while a disruption is underway.”
Not to mention keeping trucks stocked with paper logbooks…just in case. At Bison, the ransomware attack on an ELD vendor was an inconvenience; it didn’t lose any of its own data – just access to Orbcomm’s services.
An increasing target
But it could’ve been far worse, warns Shira Sarid-Hausirer, vice-president of marketing for Upstream Security, a cybersecurity firm specializing in protecting connected vehicles.
She warns the transportation sector is becoming increasingly targeted by hackers; in fact, there was a 400% increase in reported automotive cyberattacks between 2017 and 2022.
And if attacked, the loss of electronic logging capabilities could be the least of a fleet’s concerns.
“There’s something else I want to talk about, which is the fleet management solution,” Sarid-Hausirer says, noting that was also affected, interrupting a fleet’s ability to dispatch vehicles. “It’s essentially the system that controls who goes where in the fleet. Once you block the ability to communicate, which is what happened here, it means the fleet is shut down. Drivers don’t know where to go.”
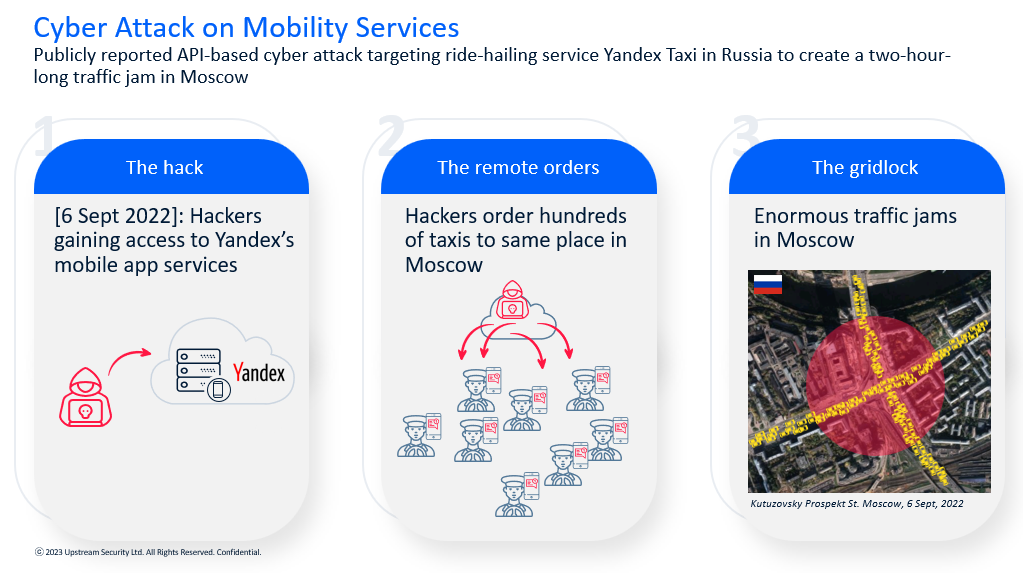
Imagine for a moment a hacker taking control of a fleet’s dispatch system and dispatching high-value loads to a location where armed bandits are waiting. Seem far-fetched? Sarid-Hausirer points to a real-life cyberattack that happened in Russia, where ride-sharing platform Yandex Taxi (a Russian take on Uber) was hacked and all drivers directed to a single Moscow location.
“The traffic jams that this created were crazy,” she said. “No vehicles were harmed in this case, and the same with Orbcomm, the trucks were fine. But they’re non-operational.”
Targeting high-value cargo
The ability to disable or reroute a truck is frightening, even more so when the truck is hauling high-value cargo.
“Let’s talk about a Brinks fleet,” Sarid-Hausirer says. “If you share just the location of the trucks, that’s a huge risk. If you share that the truck is currently not moving, that’s a huge risk. What’s the weight of the truck? I can infer from that how much money is in the truck right now.”
Lest you should think we’re giving tips to the bad guys, Sarid-Hausirer adds, “We’re not teaching them how to do their work.” They already know.
Trucking firms at risk
While the September ransomware attack that affected Bison came through a third-party supplier, fleets themselves are also at risk. U.S. LTL carrier Estes Express was stricken in early October by a cyberattack that knocked its IT systems – including phone and email services – offline for several days.
Mark Murrell, co-owner of online training firm CarriersEdge, which also administers the Best Fleets to Drive For program, began incorporating questions about cybersecurity into the program’s interview process. Why? “There are way more trucking companies getting hacked than we hear about,” he says.
And one can hardly blame hackers for targeting the trucking industry, either. If Murrell were a nefarious hacker, and not a nice guy running an online training firm, he says he’d target trucking for several reasons. Trucking is a high-dollar (if low-margin) business; firms generally have weak IT policies and management (too few people handling too many IT functions); they’re reticent to invest in modern equipment (computers and network gear – not trucks and trailers); staff receive minimal security training; and trucking companies aren’t all that worried about cyberattacks to begin with.
Cybersecurity and workplace training
“The more drivers are informed about security in general, the less likely they are to do something that compromises the company.”
Mark Murrell, CarriersEdge
But what does a fleet’s cybersecurity protocols have to do with providing drivers with a good workplace?
“There’s a perception that drivers are not at risk or don’t need to be trained [on cybersecurity],” Murrell says. “First of all, most of the time, drivers are connected to back-office systems in one way or another. And the more drivers are informed about security in general, the less likely they are to do something that compromises the company.”
Many fleets still send drivers’ personal information through email. Easy pickings for a hacker engaged in the burgeoning Fraud-as-a-Service industry, in which personal information is collected and then sold on the dark web to those looking to exploit it.
Drivers are also susceptible to phishing attacks that put themselves and their company at risk. Murrell says some hackers will scrape changes in LinkedIn profiles to target individuals who have recently changed companies and may be expecting requests for personal information from HR or other people within the company who they may not yet know.
Murrell insists trucking companies need to include every employee – including drivers – in cybersecurity training. He also encourages them to do internal audits. Have IT send a phishing email to company employees to ensure no one falls for the potential scam.
Training for all
Training for everyone in an organization is important. Bison provides training and regular communications on cyber safety fundamentals such as using strong passwords, regularly changing passwords, using multi-factor authentication when available, being cautious about clicking on links and attachments, and the importance of keeping software patched and up to date.
For a cybersecurity firm like Upstream, protection goes much further than that – especially when moving vehicles are involved. In the IT world, says Sarid-Hausirer, the goal is to detect an intrusion within a minute, understand its cause within 10 minutes, and remedy it within an hour. Seems quick, no?
“It is pretty quick,” Sarid-Hausirer responds. “But not when it’s a moving vehicle. Let’s say it’s a truck carrying cargo before Christmas. If we take an hour to figure out what happened, the damage is dramatic. And I’m not even going back to that Brinks truck example. If someone has taken over a dispatch app and is sending a truck to a place it shouldn’t go, we can’t let it happen for a full hour. It has to be blocked within minutes.”
Upstream monitors a vehicle’s OEM data and systems, third-party telematics systems, and any proprietary fleet-built apps and their related APIs. The APIs, automotive cloud, and vehicle itself are all monitored.
Increasingly connected vehicles are becoming increasingly easy to penetrate, and fleets are only as secure as their weakest link.
Be mindful of vendors
Carriers should be mindful of which vendors they choose to work with, as well. Read reviews, get references, and ask vendors about their cybersecurity stacks, Sarid-Hausirer advises.
Not surprisingly, cybersecurity was a hot topic at Isaac Instruments’ Horizon user conference in Montreal last month. Jean-Sebastien Bouchard touted the company’s ISO 27001 certification and ongoing audits as measures the company has taken to ensure its own security.
“You may think it’s not if, it’s when,” he said of potential cyberattacks. “I’ve heard that. I don’t think like this. You control the risk and you do everything you can to make sure it does not happen.”
He urged fleets to subscribe to services such as SecurityScorecard, Bitsight, Riskrecon, or UpGuard, which provide third-party analysis of the cybersecurity of various tech vendors, including ELD suppliers.
“We evaluate the companies we deal with as suppliers and how safe they are, so we don’t have a risk using their services. You should do the same thing with all the partners you’re using,” Bouchard told attendees.
Failure to take precautions could be fatal for a transportation business. Just ask KNP Logistics Group, one of the largest privately owned logistics firms in the United Kingdom, which cited a cyberattack in June as the reason for its insolvency that followed just three months later, terminating 730 positions.
“It took away their ability to raise finances and manage their financials,” Sarid-Hausirer says of the incident. “And in this case, they had to shut down because the major ransomware attack affected their key systems, processes and financial information.”
Have your say
This is a moderated forum. Comments will no longer be published unless they are accompanied by a first and last name and a verifiable email address. (Today's Trucking will not publish or share the email address.) Profane language and content deemed to be libelous, racist, or threatening in nature will not be published under any circumstances.
It seems to happen on a certain occasion and of course, the trucks these days are all controlled via electronic fancy logarithms and easy to scramble or jammed frequency to it.
If the company could email you on the fly while driving it is all of easy for scammers to get into your IP address and direct you where they want you to be.
Not only do you have to be a driver but you also have to have cyber knowledge and a security plus and plus and no real good pay it is all going for the money.
This is a great article and very thought provoking.